SAML
Nozomi Networks supports security assertion markup language (SAML) single sign-on (SSO) authentication.
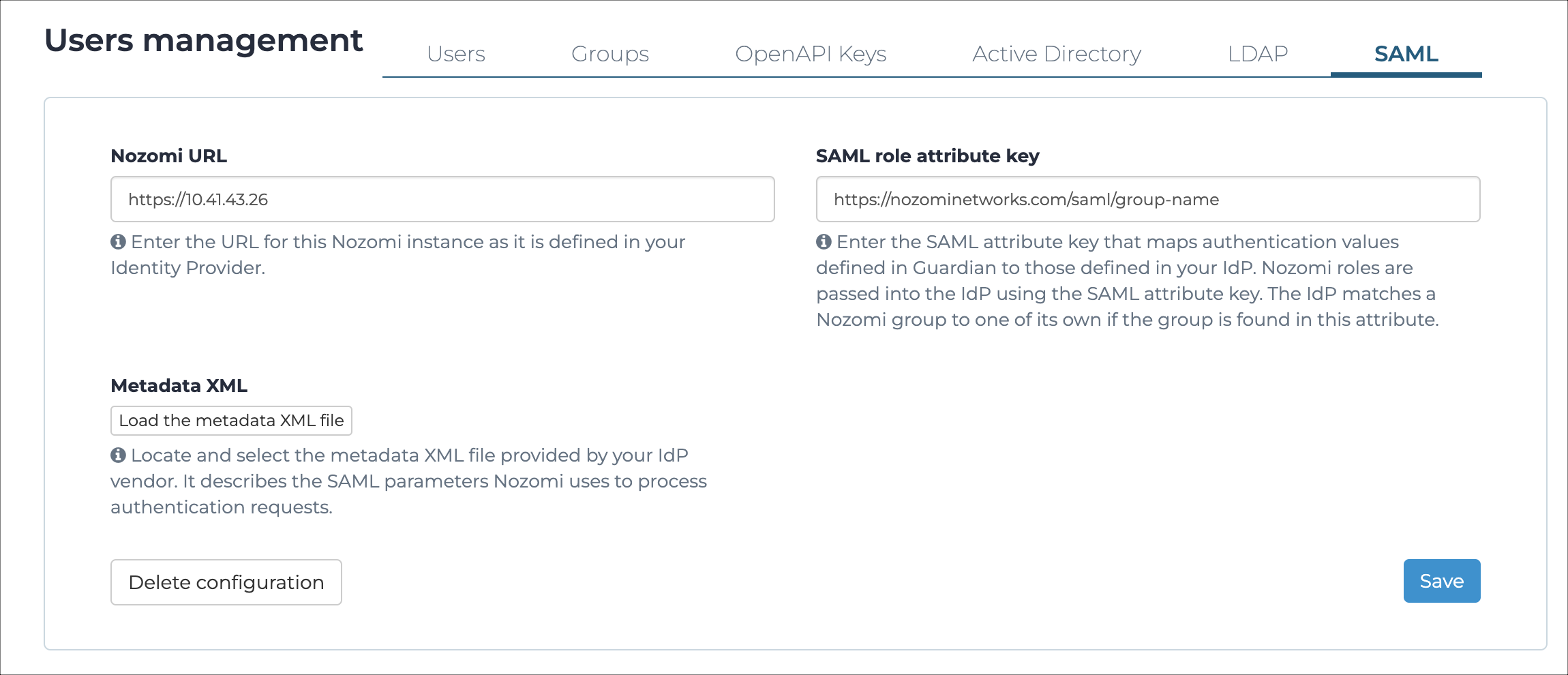
General
Your identity provider (IdP) must be compatible with security assertion markup language (SAML) 2.0.
Additional configuration
Typically, SAML with authentication, replies are sent back from the same host that originally received the request. Occasionally, SAML requests are chained between different IdPs, and replies might come from a different host. By default, the Web user interface (UI) content security rules block these types of replies.
You can use the using the csp form-action-urls configuration key to
override this behavior.
To accept replies from an IdP
single sign-on (SSO) target uniform resource locator (URL) that
differs from the one specified in the SAML metadata,
you can issue the configuration rule: conf.user configure csp
form-actionurls <additional_url> in the command-line interface (CLI).
If you need to specify more than one URL, you should use
spaces to separate them. After this change, you need to run the service
webserver stop command, in a shell console to apply it.
Clock skew
Occasionally, the IdP and CMC system
times can differ. By default, the system accepts requests with up to 60 seconds
difference. You can use the saml clock_drift configuration key to
override this behavior.
To change the value, you can issue conf.user configure saml clock_drift
<allowed_seconds> in the CLI.
After this change, you can run the service webserver stop command in
a shell console to apply it.
Limitations
The SAML logout protocol is not supported.