Zone configurations
The Zone configurations page shows all the zone configurations in your environment and lets you add new zone configurations and edit them.
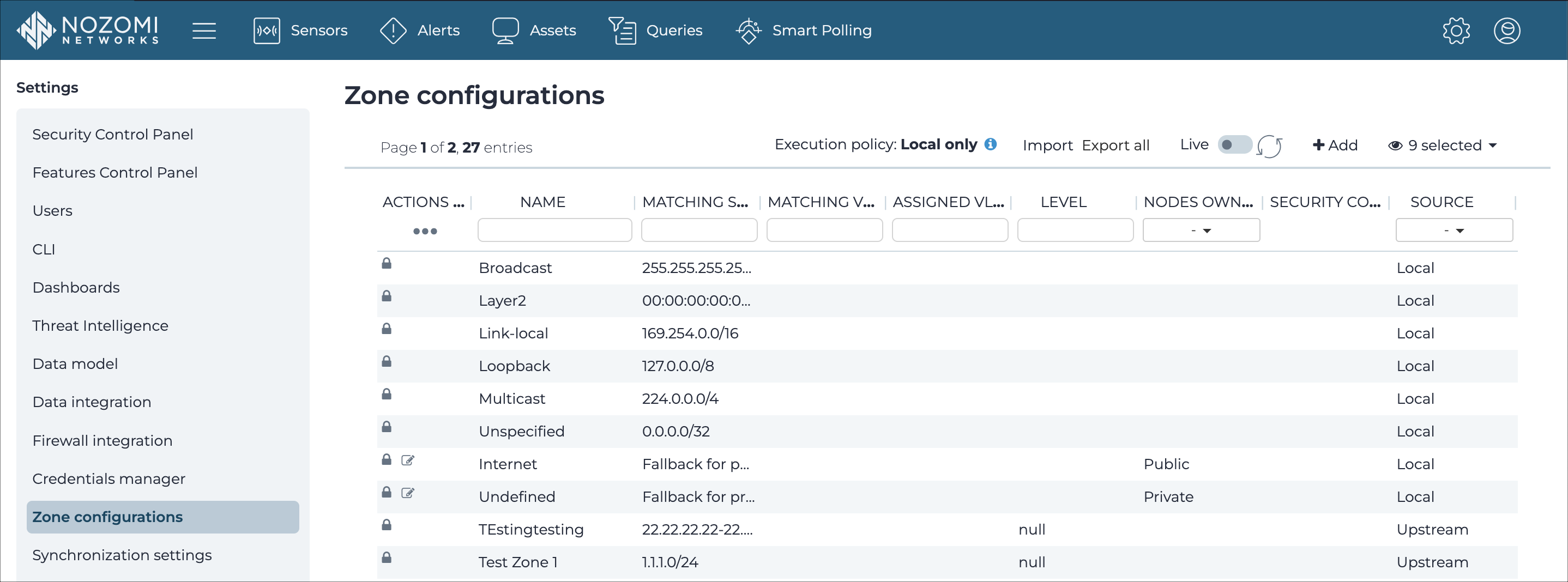
Execution policy
This shows information about the currently configured data synchronization policy.
Import
This button lets you import a configuration file (CFG).
Export all
This button lets you download a CFG of all the zone configurations.
Live / refresh
The Live
icon lets you change live view on, or off. When live
mode is on, the page will refresh approximately every five seconds.
+ Add
This button lets you add a new zone configuration.
Column selection
The columns selection icon lets you choose which columns to show or hide.
Name
The zone must be given a name without spaces. It must include at least one network segment.
Matching segments
This shows the information such as internet protocol (IP)s, IP address range, or media access control (MAC) address, matched by the node discovered within the range (only the IP range is shown in the column, not the nodes).
MAC address matching fallback
The node identifier (ID) must match the zone network segments to make the node part of zone. There are cases where this matching strategy is not enough, for example if you want to have nodes without an IP as node ID match a zone defined with MAC address ranges. In those cases we can enable this fallback matching strategy in order to match against the MAC address of the node whenever the node IP does not match a segment.
Matching VLAN ID
This only lists nodes that belong to the related virtual local area network (VLAN). This needs the VLAN tag to be extracted from the traffic.
When filtering the view with this zone, only the node 192.168.4.2 will show.
Assigned VLAN ID
Level
The level defines the position of the nodes pertaining to the given zone within the Purdue model. Once a level has been set for a zone, all nodes included in that zone are assigned the same level, unless a per-node configuration has been specified as well. This means that, if two or more zones overlap, a node that belongs to all of them will inherit the level of the most restrictive zone.
For example, if 10.1.1.1/32 belongs to Zone 1 (Level 1) and 10.1.0.0/16 (Level 2) belongs to Zone 2, then 10.1.1.1 will be assigned.
Nodes ownership
Ownership of the nodes belonging to the given zone. Once the ownership has been set for a zone, all nodes included in that zone inherit such ownership, overwriting the single nodes' ownership.
Detection approach
Used to override the global settings from the Learning section of the Security control panel.
Learning mode
Used to override the global settings from the Learning section of the Security control panel.
Security profile
Used to override the global settings from the Security profile section of the Security control panel.
Use node labels as Device IDs
This lets you use a node label, such as the computer name, as a device ID.
Network Throughput History
- last_1hour_bytes
- last_1day_bytes and
- last_1week_bytes
- last_1hour_bytes => the last hour at granularity of 5 minutes. For example, if it is 15:32 the field will cover the time span from 14:30 to 15:30
- last_1day_bytes => the last day at granularity of 1 hour, but updated every 5 minutes. For example, if it is 15:32 on Tuesday, the field will cover the time span from 16:00 on Monday to 16:00 on Tuesday and the data is updated at 15:30 on Tuesday
- last_1week_bytes => the last week at granularity of 1 day, but updated every 5 minutes. For example, if it is 15:32 on Tuesday, the field will cover the time span from 00:00 on Wednesday of the previous week to 24:00 on Tuesday of the current week, and the data is updated at 15:30 on Tuesday this week