Users endpoint
A GET to /api/open/users allows you to get a list of all the
users.
Requirements and Restrictions
- The authenticated user must be in a group having admin role.
- The result contains the list of all users.
- It's possible to use pagination adding
pageandcountparams - The
pageparam is the number of the page to return, thecountis the dimension of the page. - If count is nil or 0 the default value will be 100, if page is nil or 0 the request will not be paginated.
- This api is disabled by default; to enable it add
conf.user configure api users enabled truein command-line interface (CLI).
A GET to /api/open/user_groups allows you to get a list of all the
user groups.
Requirements and Restrictions
- The authenticated user must be in a group having admin role.
- The result contains the list of all user groups.
- It's possible to use pagination adding
pageandcountparams - The
pageparam is the number of the page to return, thecountis the dimension of the page. - If count is nil or 0 the default value will be 100, if page is nil or 0 the request will not be paginated.
A GET to /api/open/users/:id allows you to get the user having the
id passed as path parameter.
Requirements and Restrictions
- The authenticated user must be in a group having admin role.
- As last parameter of the path you need to specify the id of the user.
- The result will contain the user
- In case the user with that id is not found you'll get a 404.
A DELETE to /api/open/users/:id allows you to delete the user having
the id passed as path parameter.
Requirements and Restrictions
- The authenticated user must be in a group having admin role.
- As last parameter of the path you need to specify the id of the user.
- The result will contain the status code
204for success else the error code - In case the user with that id is not found you'll get a 404.
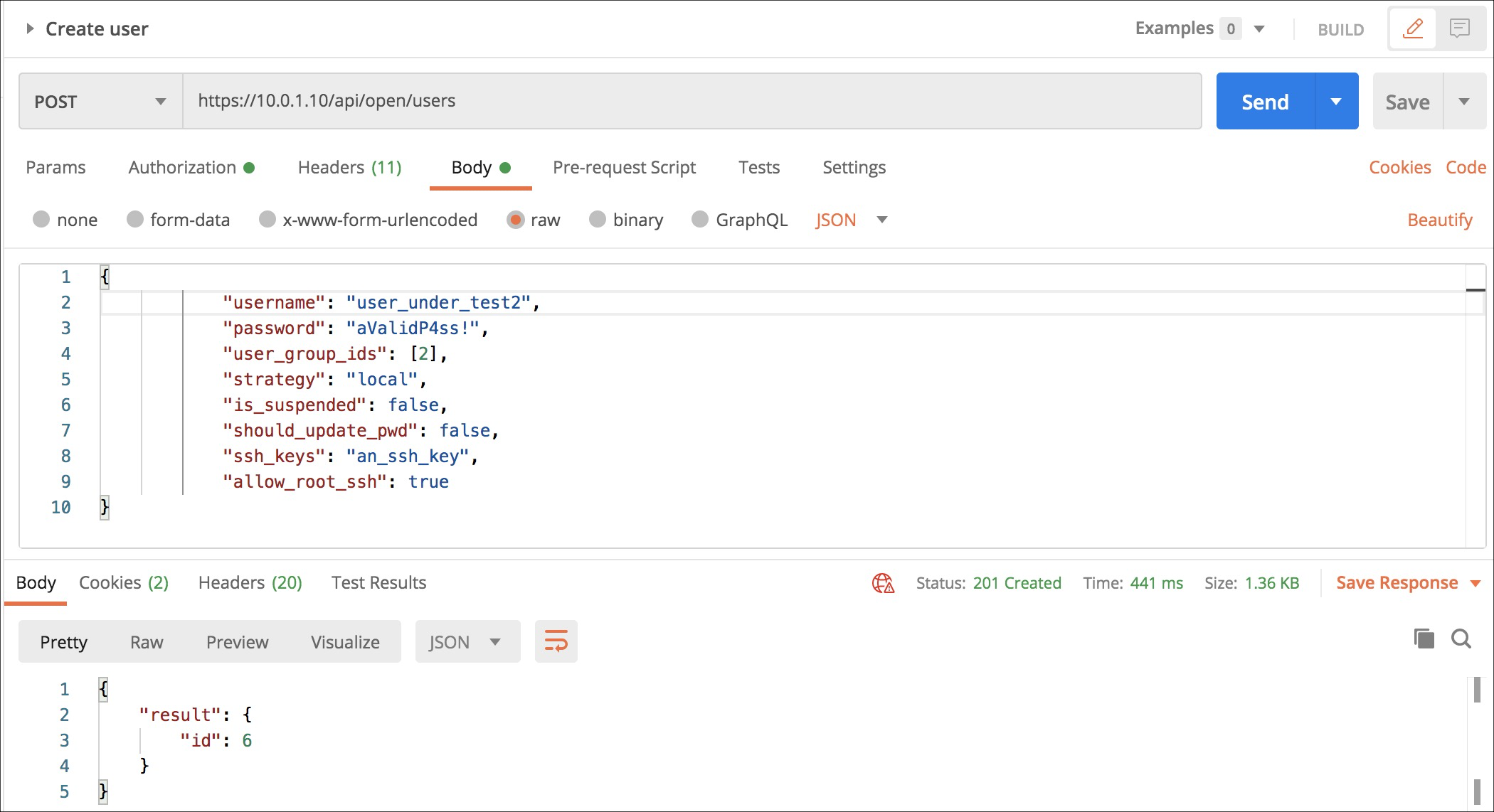
A POST to /api/open/users allows you to create a new user.
Requirements and Restrictions
- The authenticated user must be in a group having admin role.
- The input must be a JavaScript Object Notation (JSON) dictionary containing the user fields properly populated
usernameis mandatory and unique.passwordis mandatory and have to respect the password strength rules.user_group_idsis mandatory, must contain at least an id of an existing user-group.strategycan contain the value "local" or "saml".is_suspendedis a boolean.should_update_pwdtrue if the user must update the password when log-in.ssh_keysis the user secure shell (SSH) key if wants to connect via ssh to the instance.allow_root_sshtrue to allow the user having the ssh_key above to connect via SSH to the instance.- In case the request is well formed return a 201 response with the id of the user created inside the result.
{
"username": "user_under_test22",
"password": "aValidP4ss!",
"user_group_ids": [2],
"strategy": "local",
"is_suspended": false,
"should_update_pwd": false,
"ssh_keys": "an_ssh_key",
"allow_root_ssh": true
}
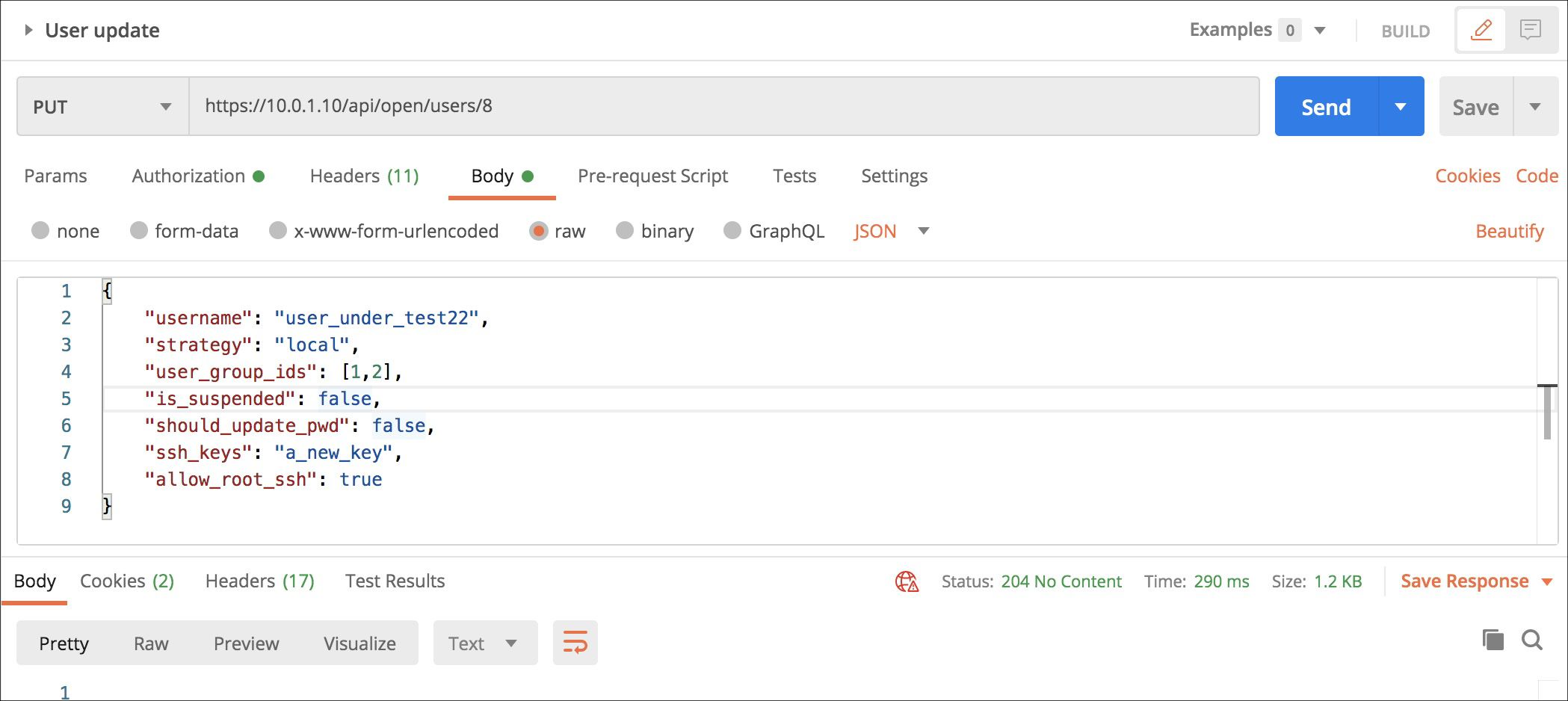
A PUT to /api/open/users/:id allows you to update the user with the
id passed as path param.
Requirements and Restrictions
- The authenticated user must be in a group having admin role.
- As last parameter of the path you need to specify the id of the user you want to update.
- The input must be a JSON dictionary containing the user field properly populated
- If the update goes well the call return 204 (No content) response
- You can't update the password here because updating password is not idempotent so you can't do via PUT.
- The fields you can update are listed below.
user_group_idsmust contain at least one valid id.
{
"username": "user_under_test22",
"strategy": "local",
"user_group_ids": [1,2],
"is_suspended": false,
"should_update_pwd": false,
"ssh_keys": "a_new_key",
"allow_root_ssh": true
}
A PATCH to /api/open/users/:id/password allows you to change the
password of the user having the id passed as path param.
Requirements and Restrictions
- The authenticated user must be in a group having admin role.
- The user id should be passed in the path.
- You need to pass the new password in the body.
- New password must respect the password strength rules.
- In case the password is valid will be return an empty response with status code 204.
{
"password": "4ValidP4ssw0rd!"
}