Threat intelligence
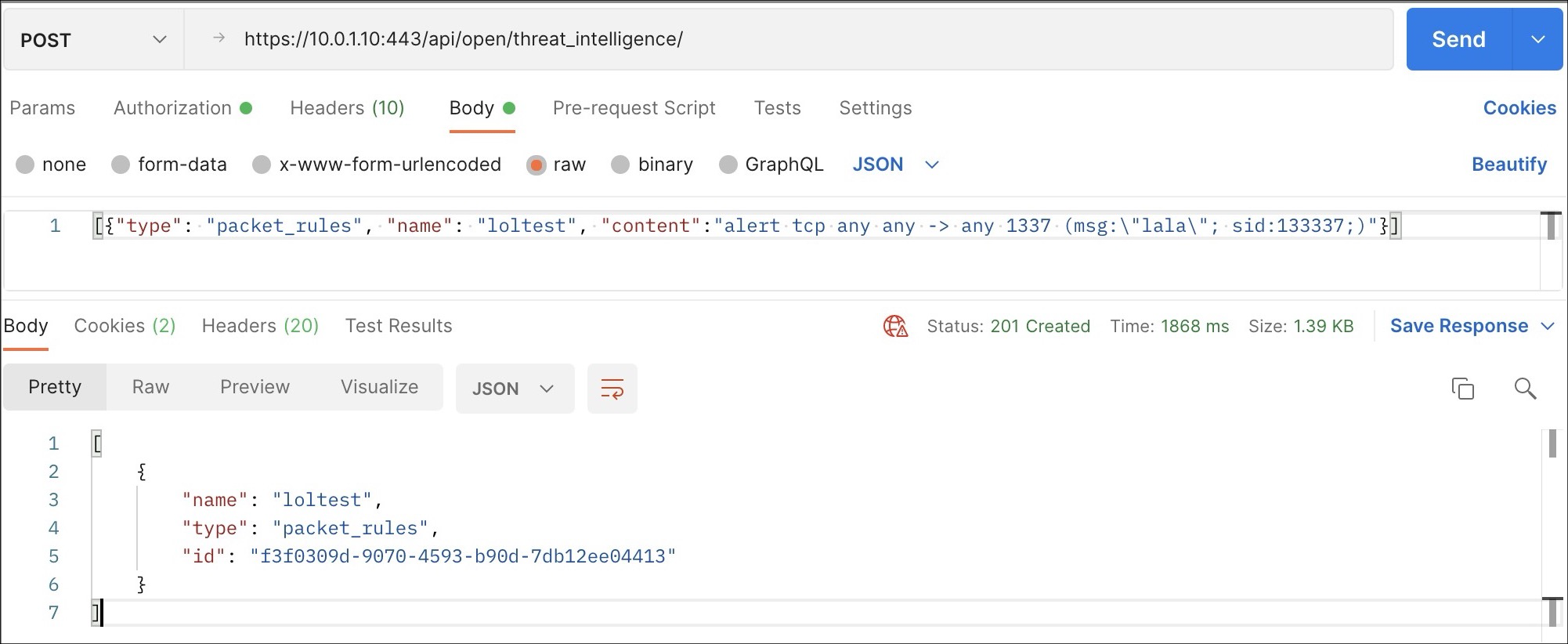
A POST request to /api/open/threat_intelligence allows you to create
indicators.
Requirements and restrictions
- An authenticated user must be in an admin role group or belong to a Threat Intelligence group with the Allow configuration option switched to ON in the group settings.
- JavaScript Object Notation (JSON) content is represented as a array of contents that allows you to insert more than one (1) indicator at a time.
- Type of content must be specified in the
typeparameter and the value must be:packet_rules,yara_rulesorstix_indicators. - Content name must be specified in the
nameparameter. - The content must be specified in the
contentparameter. - If the request is accepted, the result contains the
resultwith an identifier (ID) as value. - The request is rejected if the sensor is connected to a Central Management Console (CMC).
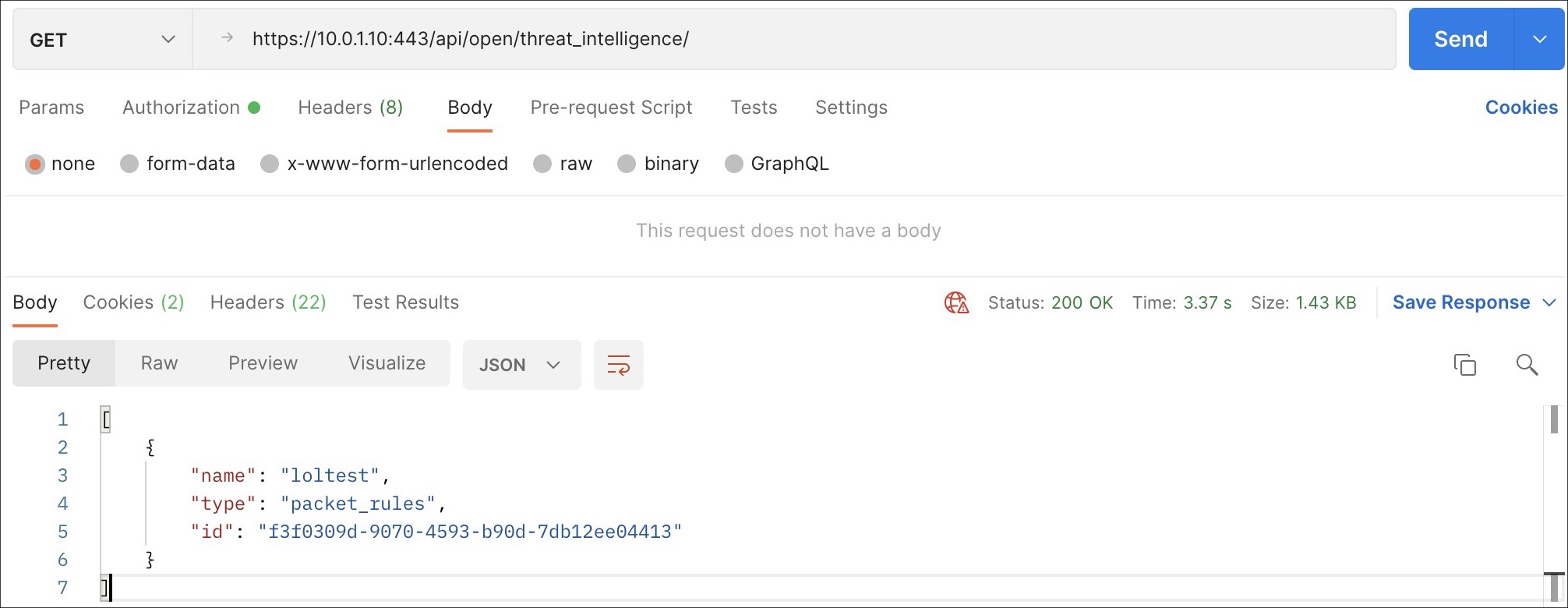
A GET request to /api/open/threat_intelligence allows you to list
indicators created by the user.
Requirements and Restrictions
- An authenticated user must be in an admin role group or belong to a Threat Intelligence group.
- If the request is accepted, the result contains a Json array of contents with
id,nameandtype.
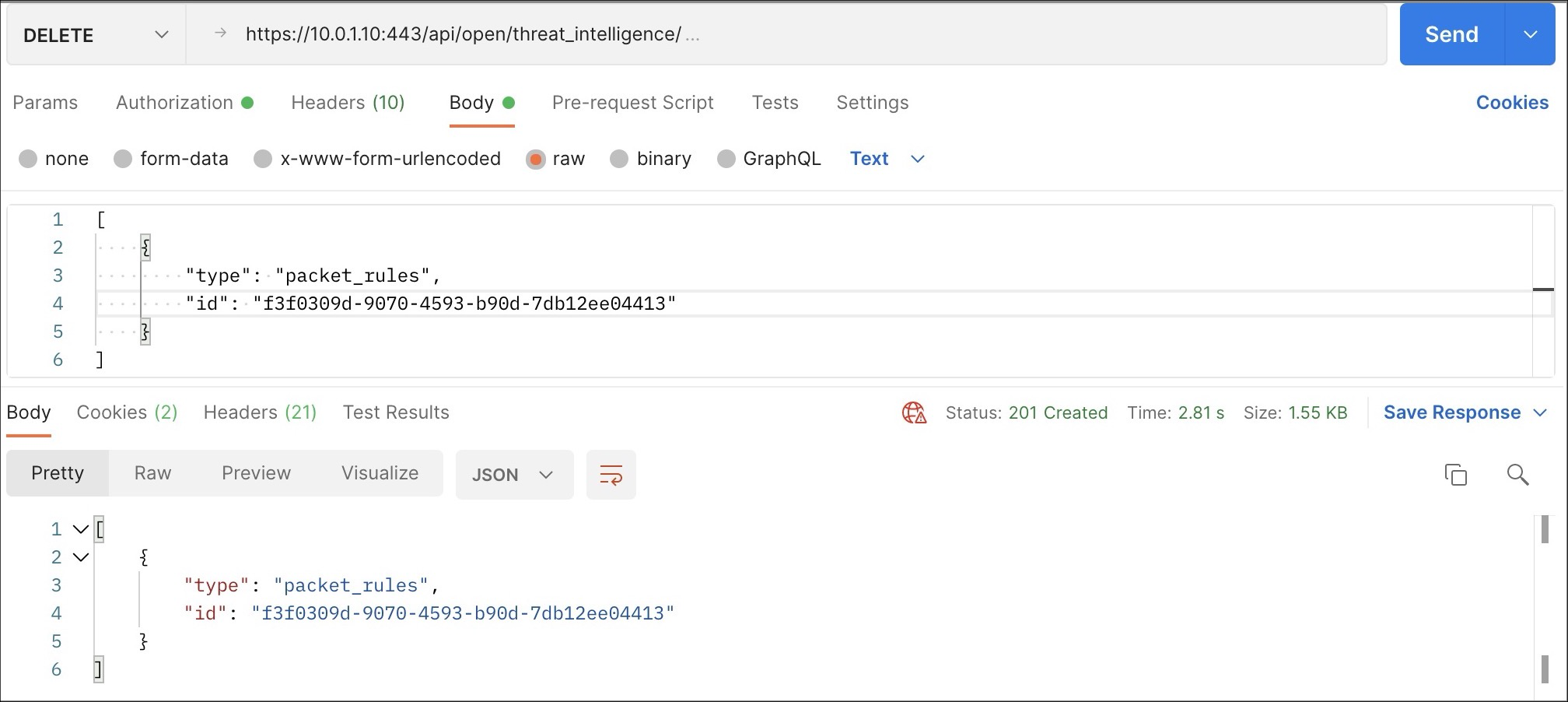
A DELETE request to /api/open/threat_intelligence allows you to
remove indicators.
Requirements and restrictions
- An authenticated user must be in an admin role group or belong to a Threat Intelligence group with the Allow configuration option switched to ON in the group settings.
- The Json content is represented as an array of contents that allows you to remove more than one (1) indicator at a time
- The type of content must be specified in the
typeparameter and the value must be:packet_rules,yara_rulesorstix_indicators. - The content id must be specified in the
idparameter. - If the request is accepted, the result contains contents with
idandtype. - The request is rejected if the sensor is connected to a CMC.