Details page
The Alerts details page provides a comprehensive view of a triggered alert, including cause, context, and recommended response. It displays communication paths, affected nodes, and relevant MITRE ATT&CK tactics. Use this page to investigate incidents and track alert handling activity.
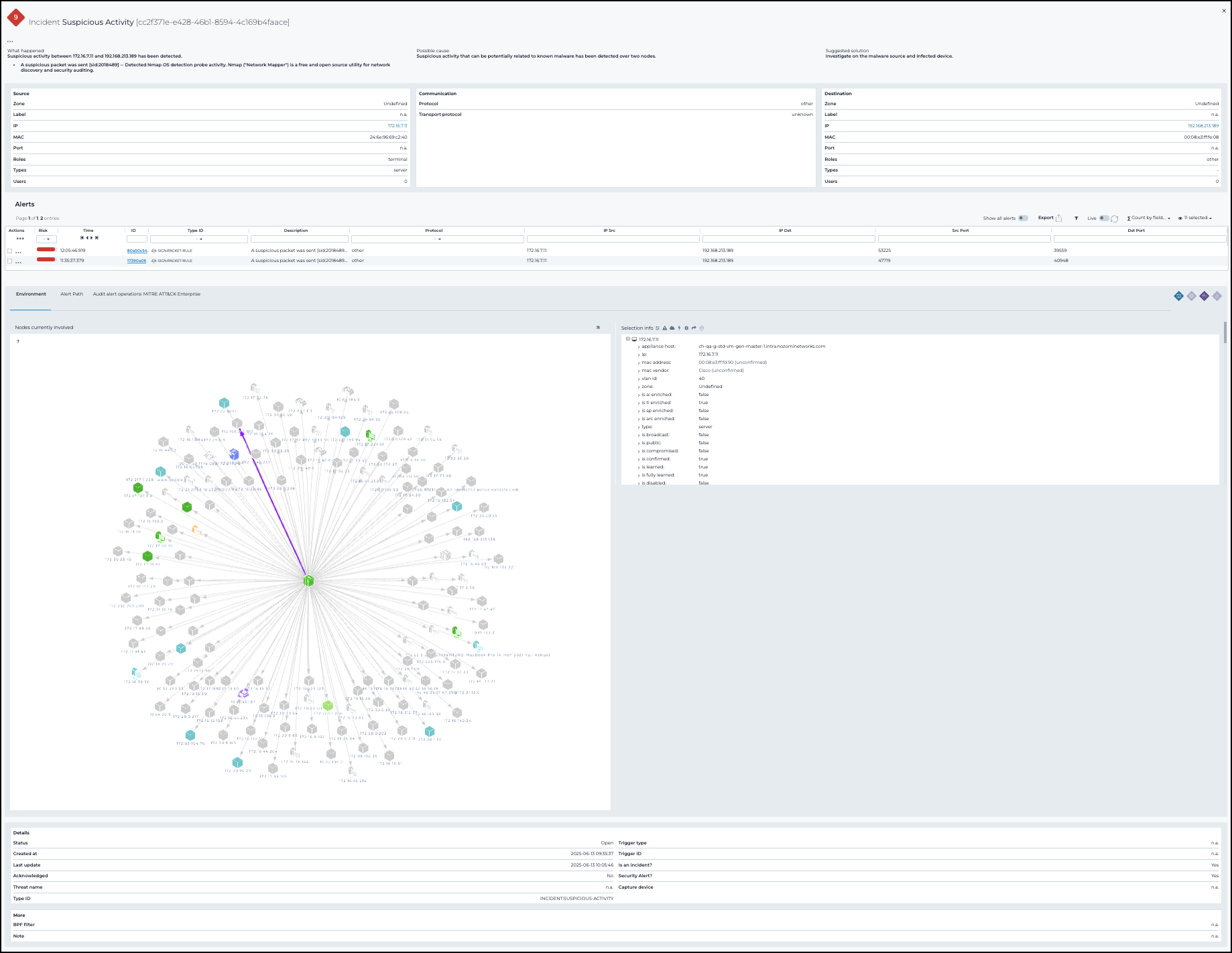
What happened
Shows a summary and a list of key details for the related alert.
Possible cause
Shows a possible cause of the alert.
Suggested solution
Our recommendation on the best way to solve the problem.
Environment
Shows a graph with the logical connections for the related nodes. The Selection info section shows all the applicable information for the alert. It also gives you access to the actions menu.
Alert Path
The Alert Path view displays the physical connection path between source and destination devices involved in a triggered alert. This path is traced at the cable level, including intermediate switches and any other devices connected along the route. The alert path shows with a red line.
This view helps users assess the potential impact of response actions, such as disabling a specific switch port to isolate a device. By identifying additional assets that share the same physical infrastructure, operators can evaluate containment strategies and take targeted action directly from the alert interface.
Audit alert operations
The Audit alert operations section shows a timeline of user or system actions taken on a specific alert. This section helps you track how an alert is handled throughout its lifecycle.
It records these types of activity:
- Acknowledgement of the alert
- Escalation of the alert to an incident
- Changes to the alert’s severity or classification
- Notes or comments that were added
- Automatic responses or triggered workflows, if the system is integrated with them
MITRE ATT&CK Enterprise
The MITRE ATT&CK for ICS section helps security analysts understand how the current alert maps to known tactics and techniques used by threat actors in industrial control systems (ICS) environments.
This section shows which tactics from the MITRE ATT&CK for ICS framework are relevant to the alert. The tactics represent different stages of an attack lifecycle, such as:
- Initial Access
- Execution
- Persistence
- Evasion
- Discovery
- Lateral Movement
- Collection
- Command and Control
- Inhibit Response Function
- Impair Process Control
- Impact
Each tactic can display one or more techniques observed in the alert. This mapping helps analysts determine the attacker's goals and possible next steps.