Configuration
The Configuration page lets you define upstream connection settings, execution options, protection preferences, and traffic monitoring parameters for the Arc sensor.
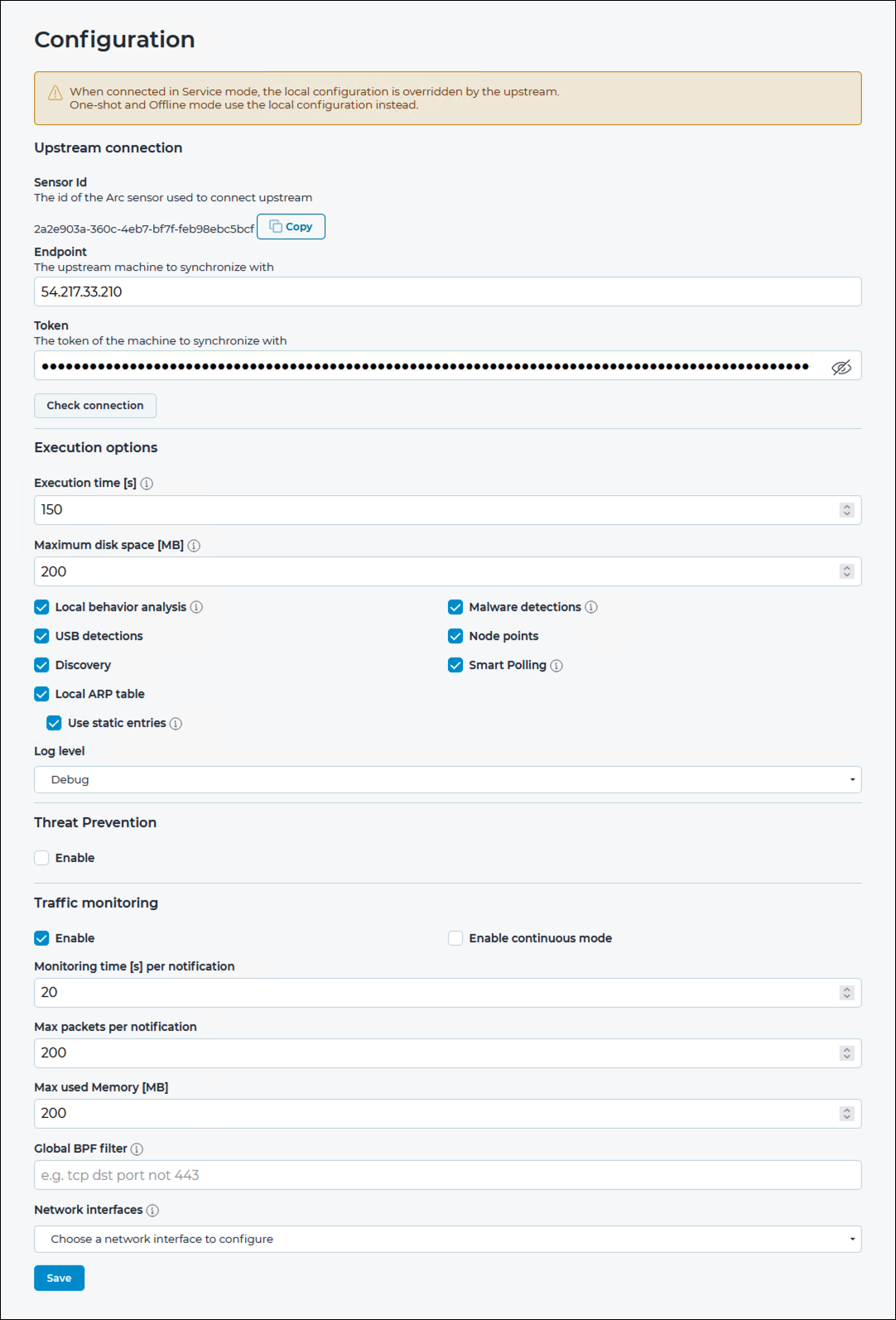
The Configuration page has these sections:
The Configuration page lets you define upstream connection settings, execution options, protection preferences, and traffic monitoring parameters for the Arc sensor.

The Configuration page has these sections: