Host-based intrusion-detection system
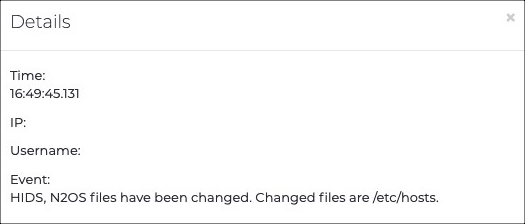
The internal Host-based intrusion-detection system (HIDS) sensors detect changes to the basic firmware image and note the change.
When a change is detected in the sensor's basic firmware image, a new event is logged in the system's audit log. It is also replicated in Vantage or the Central Management Console (CMC).
You can change the default host-based intrusion-detection system (HIDS) settings to suit your security requirements.
Note:
This feature is not available in the container version due to
the different security approach.
| Parameter | Default value | Description |
|---|---|---|
| hids execution interval | 18 hours | HIDS check execution interval |
| hids ignore files | - | Coma separator list of files to be ignored by HIDS (ex: /etc/file1, /etc/file2) |